Basics
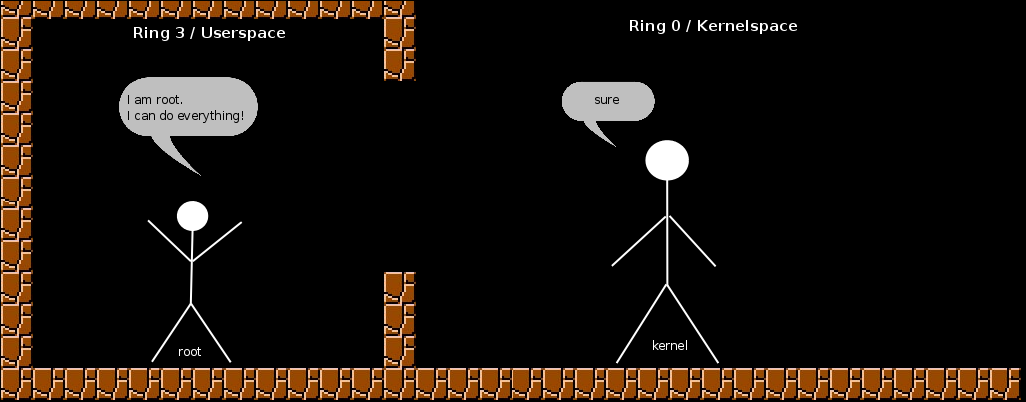
The computer is devided into two parts: Userspace and Kernelspace.
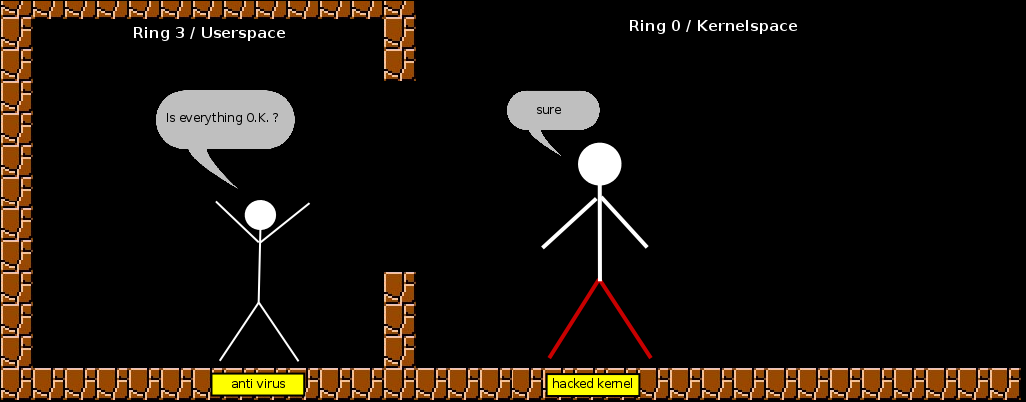
Every program (Firefox, VI, bash, gimp...) runs in userspace. But it can not access any data, the only way to send/save or receive/open data is the kernel (more exactly, the syscall interface). It's indicated by the guy standing in the room, with walls all around him.
The Kernel is mightier than root, but barely does something on its own, it's like a slave to the userspace. He has all the access, eg, can read and write to any hardware (graphic card, network card, harddisc, dvd etc...).
Every program (Firefox, VI, bash, gimp...) runs in userspace. But it can not access any data, the only way to send/save or receive/open data is the kernel (more exactly, the syscall interface). It's indicated by the guy standing in the room, with walls all around him.
The Kernel is mightier than root, but barely does something on its own, it's like a slave to the userspace. He has all the access, eg, can read and write to any hardware (graphic card, network card, harddisc, dvd etc...).